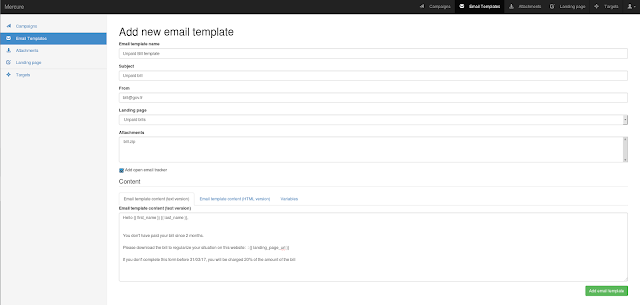
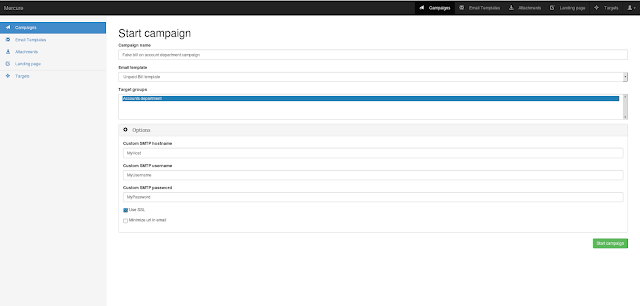
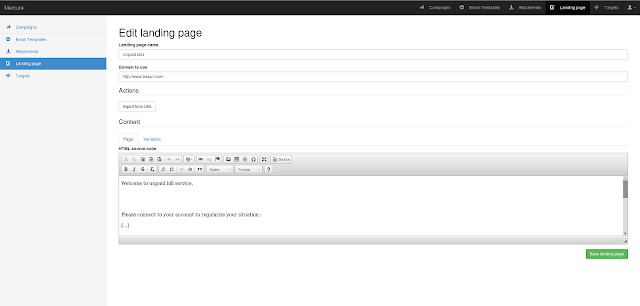
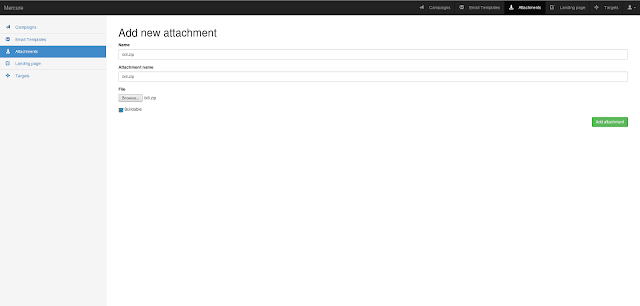
A very fast network logon cracker which supports many different services.
See feature sets and services coverage page - incl. a speed comparison against ncrack and Medusa. Number one of the biggest security holes are passwords, as every password security study shows.
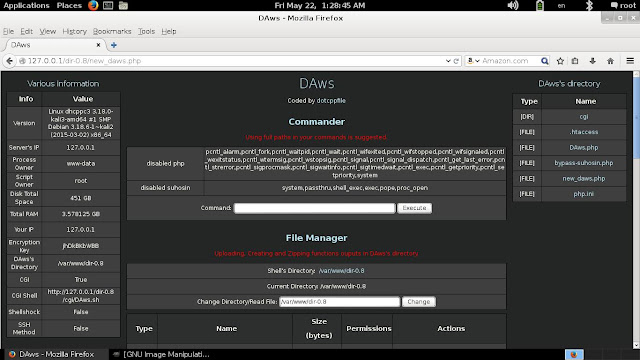
This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system.
There are already several login hacker tools available, however, none does either support more than one protocol to attack or support paralyzed connects.
It was tested to compile cleanly on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX (Blackberry 10) and OSX.
Currently, this tool supports the following protocols:
Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
CHANGELOG for 8.6
CHANGELOG for 8.6
===================
! Development moved to a public github repository: https://github.com/vanhauser-thc/thc-hydra
! Reports came in that the rdp module is not working reliable sometimes, most likely against new Windows versions. please test, report and if possible send a fix
* added radmin2 module by catatonic prime - great work!
* smb module now checks if SMBv1 is supported by the server and if signing is required
* http-form module now supports URLs up to 6000 bytes (thanks to petrock6@github for the patch)
* Fix for SSL connections that failed with error:00000000:lib(0):func(0):reason(0) (thanks gaia@github for reporting)
* Added new command line option:
-c TIME: seconds between login attempts (over all threads, so -t 1 is recommended)
* Options put after -R (for loading a restore file) are now honored (and were disallowed before)
* merged several patches by Diadlo@github to make the code easier readable. thanks for that!
* merged a patch by Diadlo@github that moves the help output to the invididual module
 0Day to Buy
0Day to Buy